Veriato Cerebral: AI-Powered Insider Threat Detection & Response
Protect your critical business data with a software that combines user behavior analytics and user activity monitoring

Protect your critical business data with a software that combines user behavior analytics and user activity monitoring
Veriato Cerebral is an AI-powered security platform that integrates User & Entity Behavior Analytics (UEBA) with User Activity Monitoring (UAM) which allows rapid Data Breach Response (DBR). With Cerebral, you’ll have the ability to identify risks early on.
It immediately alerts you to who is exhibiting signs of risk, shows you related screen shots so that you can immediately determine the true nature of the incident. This level of visibility empowers you to rapidly take action with 100% confidence – all while gathering essential evidence.
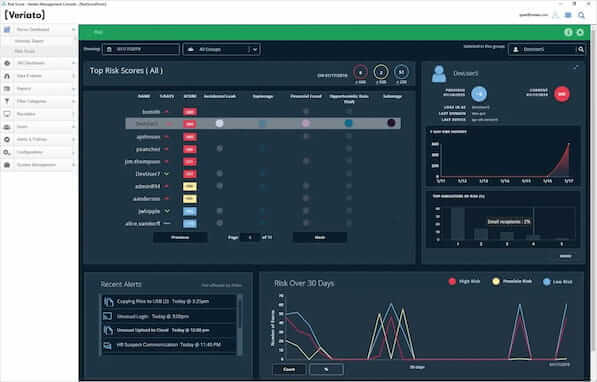
Cerebral’s AI-based behavior analysis continually tracks each user's activity and language to create their daily risk score. The Risk Score dashboard shows high scores for each day, trends, recent alerts, and user details. It provides an immediate overview of high risk, user behavior within your organization.
With up to 60% of breaches coming from insider threats, it’s critical that corporations proactively monitor all endpoints for the rapid detection of internal breaches.
Lengthy investigations are a thing of the past with Veriato Cerebral. Now, you can identify suspicious activities, react in minutes, notify HR, management, operational security, and even law enforcement.
With up to 60% of breaches coming from insider threats, it’s critical that corporations proactively monitor all endpoints for the rapid detection of internal breaches.
Cerebral monitors and analyzes all user activity at the endpoint, including web & dark web activity, compromised credentials, email activity, chat & IM, psycholinguistics, network activity, file & document tracking, keystroke logging, application activity, geolocation, user status, and more.
Veriato AI (UEBA) continually scrutinizes all users’ activity and sentiment, watching for anomalies in behavior compared with their personal baseline or that of a specific group. Additionally Cerebral will watch for outsiders trying to access the network with stolen credentials.
Cerebral immediately notifies your security team when it identifies a threat. With an extremely low false positive rating (<2%). Cerebral’s alerting maximizes the efficiency of the security team by eliminating the need to have people constantly monitoring employees, hoping to find an issue.
Cerebral's Time-Capsule DVR gives you the ability to look directly at a video of the user’s screen as they open files, download data, or surf the internet. This is invaluable in rapidly determining whether the user’s actions are benign, a hazardous mistake or deliberately malicious.
Cerebral’s video playback allows you to react immediately and with 100% confidence. The screen recordings can also be exported as timestamped images or video files, creating vital evidence in inter-company disciplinary action as well as in legal proceedings. Veriato's detailed logs, reports, images, and video evidence have been used in hundreds of cases worldwide to prosecute malicious insiders successfully.
Windows OS 10, 8.1, 8, 7
Windows Server 2016, Server 2012, Server 2008 R2
Mac OS X: 10.15 Catalina, 10.14 Mojave, 10.13 High Sierra, 10.12 Sierra, 10.11 El Capitan
Android OS 9, 8, 7, 6, 5
Support has been tested on:
Blackberry Motion (9.0)
Motorola G6 (8.0)
Motorola E4 Plus (7.1.1)
Motorola Moto E4 (7.0)
BlackBerry Motion (7.1.2)
BlackBerry DTEK50 (6.0.1)
Samsung Galaxy S7 (6.0.1)
Motorola Nexus 6
Motorola Nexus tablet
Samsung Galaxy A5 (5.0.1)
The Recorder is optimized to be virtually unnoticeable at the computer. A Veriato Cerebral Recorder requires about 1.5 GB free disk space on computers or 145 MB on mobile devices. More may be used, depending on level of activity, recording settings, and the device’s ability to upload to the server.
Unless you tell it not to, the Recorder continues to record while off the network. As soon as the computer re-connects to the server network, it uploads its stored data.
A single Veriato Management Console handles ten of thousands of computers, and many more are possible using special methods. Contact Veriato Sales for information.
Very likely not. The files are hidden and can be obscured further with naming and location options. That said, if an expert user happens to find a component and disable the software, a system alert will warn that the client is down.
You can record any computer that meets the Recorder system requirements. Applications, console sessions, file transfers and network connections initiated by the server are recorded.
Can I record Citrix or Terminal Services hosted sessions?
Yes. Add a Recorder to your virtual machine OS templates, and as long as any new VMs use computer names that have been licensed under Veriato, the Recorder will activate with each new session. More Detail
Following successful Recorder installation, you might wait 10 minutes to see data in the Management Console. Once it gets going, a Veriato 360 Recorder uploads data every four minutes, and the server processes it every few minutes. Status normally appears for a user 5-10 minutes following action at the computer.
In Management Console logs, Total time is the duration a program instance or website was open, Focus time is the duration the instance or web page was the front window on the desktop, and Active time is the duration someone was actively clicking, typing, or scrolling in the focus window.
Cerebral provides the option of alerting immediately on keywords, on changes in user behavior (anomalies), or on any condition met in data fields (events). You choose the activity to watch, parameters for alerting, who to watch, and actions taken when an alert is triggered.
Yes. The Data Explorer or User Screenshot viewer allows you to select a set of frames and output the selection to movie format.
The Management Console Configurations | Exportoption provides the ability to pump data as CEF or SYSLOG output to SIEMs, such as Splunk and ArcSight. Another add-on Export Utility allows automatic output to standard file formats. Most 360 data views provide means to export the current view to several file types.
No. Veriato communicates with your installation for licensing and update purposes only. There is no view into your secure database and files.
Initial analysis takes longer than ongoing analysis because patterns of behavior need to be detected and calibrated. Expect about 30 days to pass before you get reliable data for newly recorded users in the Recon Dashboard. Once patterns are calibrated, the analysis is continuous and updated daily.
These groups form organically based on resources used by people on the network. Just sit back and see what happens. You’ll get a picture of the kind of work happening and whether or not people are acting within their roles. You can use these groups as the basis for anomaly reporting.
Check the machine or virtual machine for base requirements:
IMPORTANT: The Veriato Setup will not install to RAM or to a read-only, mapped, compressed, or removable drive. If the setup cannot determine the drive type, the installation will not be allowed.
For evaluation or small installations with 10-50 endpoints, you can use a Quick Install or an Advanced Install with the provided SQL Server Express instance. If SQL Express is already installed on the machine where you are installing, the setup creates a new instance named VERIATO360. If a VERIATO360 instance already exists, the setup will not proceed.
NOTE: The Veriato Setup checks for minimum free disk space requirements. SQL Server Express data and log files will be directed to the default location under the named instance – VERIATO360.
Quick Install with SQL Server Express | |
Hardware | Windows Professional/Server 64-bit OS: Business-class Desktop: Quad-Core Xeon with min. 8 GB RAM |
Prerequisites | .NET Framework 4.7.1 provided |
Quick Install to drive C:\ | 61 GB free hard disk space to install |
Advanced Install with SQL Server Express | |
System drive C:\ | 5 GB free on C:\ system drive
|
SQL Server Express drive | 50 GB free disk space |
Cerebral Server drive | 650 MB free disk space |
Management Console drive | 200 MB free disk space |
File Storage | 5 GB free disk space |
* Be sure you have the latest OS updates.
Use an Advanced Install and select an existing instance for a fully expanding SQL Server database.
See Upgrading for free disk space required to perform an upgrade.
See Server Sizing for requirements for ongoing use based on number of users/devices.
Advanced with Existing Instance – Server Requirements | |
Veriato Cerebral Server | Windows Professional/Server 64-bit OS: Business-class Desktop: Quad-Core Xeon with min. 16 GB RAM |
Server Prerequisites | .NET Framework 4.7.1 provided |
System drive C:\ | 5 GB free disk space |
Server Disk Space | 1 GB Veriato Cerebral Server 200 MB Veriato Cerebral Management Console application |
File Storage | Local to the primary server or shared among multiple servers. |
* Cerebral includes 9 component/services that maintain logs for the last 7 days.
Prepare your Cerebral database instance. The following table shows minimum requirements for installation.
Advanced with Existing Instance – Database Requirements | |
SQL Server Instance | Windows Professional/Server 64-bit OS: 16 GB RAM |
Database Instance | Microsoft SQL Server 2016 SP1/SP2 Standard or Enterprise SQL Server collation: SQL_Latin1_General_CP1_CI_AS |
Database Disk Space | 250 GB free to install and configure Cerebral databases: 50 GB free on system volume 120 GB free on instance volume – DATA location* 40 GB free for logs – LOG location* 40 GB free recommended for backups – BACKUP location* |
*IMPORTANT: We recommend maintaining at least half the size of the VeriatoReporting database in free disk space at each of these locations.
You can install multiple Management Consoles for managers that communicate with the primary Veriato Cerebral Server and database. In this case, use a Management Console Only installation.
Management Console Only | |
Management Console | Windows 7 SP1, 8, 10 |
Hardware | Minimum: Two processors or dual-core single processor. |
Prerequisites | .NET Framework 4.7.1 (installed if necessary, requires restart) |
Hard drive disk space | 200 MB |
Monitor resolution | 1280 x 1024 or higher is optimal |
Communication | Access to the Veriato Cerebral Server at port 54709. |
Platform | Operating System |
| Windows 10 Windows 8.1 Windows 8 Windows 7 Server 2016 Server 2012 Server 2008 R2 Server 2008 |
11 Big Sur 10.15 Catalina 10.14 Mojave Earlier versions may be partially recorded. | |
Android OS 9 – Pie Android OS 8 – Oreo Android OS 7 – Nougat Android OS 6 – Marshmallow |
We are always ready to answer your questions and tell you more about what this solution can do for your organization – you can also schedule a FREE online or on-site demo with us!
Fill out the form below to download.
Fill-out the form on your right to inquire about Veriato Cerebral or schedule a FREE Demo!